Beware Ransomware: Our Guide To Computer Monitoring Software
In recent news about computer monitoring software, KP Snacks announced that they were the victim of a Ransomware hack. In a letter sent out to retailers, the company announced that it “cannot safely process orders or dispatch goods”. KP Snacks is just the latest target of hackers using ransomware and computer monitoring software. As we delve deeper into the subject of computer monitoring, we will reveal just how easily a system can fall victim to dangerous software. But worry not. We also explain how you can protect yourself with counter-surveillance Spy Equipment devices.
What Are Ransomware Hacks?
Ransomware hacks involve infecting the chosen victim’s system with a particularly nasty type of monitoring software. The data security of even internationally renowned companies is often breached to install this vicious malware in the simplest of ways.
Phishing spam is the most common way this is achieved. Attachments containing ransomware and software for monitoring computers are included in an email, often one that is designed to look exactly like one the victim would trust. As soon as they click the link and download the malware it begins spying on the victim’s computer, soon after taking it over completely.
More cunning computer hackers may also use social engineering to circumvent data security systems without even needing to install computer monitoring software directly. Outlined by Chris Nickerson in the article The Anatomy Of A Hack, this method can be as simple as a nefarious yet charming computer hacker contacting the victim over the phone and impersonating someone trustworthy. Using knowledge of current events and even information that is publicly available on social media, they can convince an unwitting employee to give up their login details. No monitoring software required. The hacker can spy on the computer system at their leisure, with the victim not realising until it’s far too late that they’ve been had.
More aggressive types of ransomware can be even more dangerous. Computer monitoring software such as the NotPetya Virus spreads on its own, without the need for tricks or even human intervention. This particularly nasty piece of software takes advantage of security flaws in Windows, and uses them to access network admin credentials hidden in the infected computer’s memory. The software then spreads itself to monitor all computers on the local network.
What Does Computer Monitoring Software And Ransomware Do?
As experienced providers of data security & computer data recovery spy devices, as well as counter-surveillance equipment, we at Spy Equipment UK are well informed about the serious threat of computer monitoring software and ransomware. When it comes to the safety and security of our customers, we take no shortcuts in our research.
Computer monitoring software is exactly what it sounds like. Software that allows the user to spy on all activity on the target computer. By itself, this is not necessarily dangerous. Many companies use some form of computer monitoring software to keep track of the productivity of their workers, and ensure they stay off of elicit websites during working hours.
When you should be concerned about monitoring software on your computer is when it begins to track important activities, documents, and keystrokes. Someone who has secretly installed monitoring software to spy on your computer could use it to see bank details, company secrets and any and all private messages that you send, therefore, giving them access to your entire virtual life.
Ransomware takes it one step further. Typically, once hackers have access to the target system ransomware is used to lock users out entirely and encrypt critical information held on the network. This can have a devastating impact on the victim, particularly if it is a complex business attempting to maintain operations.
These files can no longer be decrypted without a mathematical key known only to the hacker. The victim will then be presented with a message explaining exactly what information they’ve been locked out of, and exactly who and how much they need to pay to get it fixed. Usually, this is done in an untraceable Bitcoin payment. Often, a victim does not realise they are the target of a monitoring software computer hack until they are asked to pay up.
Spy Equipment Data Security Devices To Protect You Online
At Spy Equipment UK, we are keenly aware of the danger many people face from hackers every day online, and so we’ve picked out two data security devices from our Data Security and Computer Data Recovery ranges that are best suited to conduct pre-emptive and counter surveillance to protect your data. We have even included a third option for those already suspicious that they are a target of hackers using computer monitoring software. Here are our chosen data security devices:
The Cloakey Online Privacy Tool- £174.00
The Cloakey Online Privacy Tool is a recent addition to our spy equipment store, and not a minute too soon. This data security device specialises in protecting any computer you plug it into from dangerous hackers who might attack with ransomware or computer monitoring software. This makes it perfect for a security conscious individual working both in the office and from home.
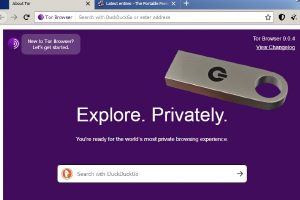
The easily transported usb stick contains specialist security software to prevent anyone from spying on your computer. It is also easy to use. Simply plugging the device in presents you with a suite of data security options to protect yourself online, ranging from the totally anonymous TOR browser to providing a password manager with a secure notepad, meaning your login details are completely safe from data breaches and malicious monitoring software computer hacks.
The Windows Master Key – £178.80
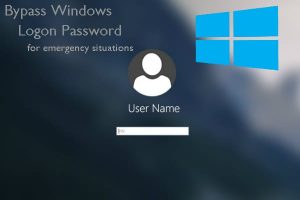
The Window Master Key is another data security counter surveillance device you will want to have in your back pocket. Not to be mistaken for a simple password recovery tool, when plugged into a windows computer this spy device will completely circumvent the need to input a password at all. This makes it ideal for situations where someone has used a keylogger in computer monitoring software to steal and then change your passwords. This data security counter surveillance device can therefore make all the difference between regaining access to your files and losing them forever.
Counter Surveillance Sweep Service
In this article we have listed just a small number of the ways criminals may try and steal your important data monitoring software computer hacks. With spy technology advancing at such a rapid pace, even a well-informed civilian may struggle to protect themselves from each and every threat. That’s why we’ve added one more thing to our list.
Spy Equipment UK offers a Counter Surveillance Sweep Service. Whether it’s a competitor trying to steal critical information about your business, or a jealous spouse attempting to monitor your activity, when it comes to protecting your personal information from hackers, it’s best to bring in a professional.
Our Counter surveillance sweep service is spearheaded by a veteran ex-policeman and private investigator with years of field-experience and industry knowledge. Even the police contact us for our expertise on counter surveillance techniques. So if you truly are worried about hackers, spies, ransomware, and computer monitoring software, give yourself total piece of mind with this service.
Am I At Risk From Hackers Using Computer Monitoring Software?
There’s good news and bad news. These kinds of Ransomware attacks are typically focused on large organisations that can be squeezed for huge amounts of money; such as healthcare organisations or financial institutions. But in the wake of the pandemic more and more people are working remotely online, and hackers have responded with a huge rise in attacks using computer monitoring software to steal important personal and company data.
Spy Equipment UK- Protecting You With The Latest Data Security Devices
If you have a need for counter surveillance data security devices, please get in touch with our expert team of private investigators and ex-police officers. Contact us on 024 75601 0588 and we’ll be glad to see to your data security device needs.